Cell C Cyber Security Breach: Impact, Investigation, And Mitigation

Premium Photo | Cybersecurity breach alert hacked message on digital - Source www.freepik.com
Editor's Notes: "Cell C Cyber Security Breach: Impact, Investigation, And Mitigation" have published today date". Give a reason why this topic important to read.
Explain our effort doing some analysis, digging information, made Cell C Cyber Security Breach: Impact, Investigation, And Mitigation we put together this Cell C Cyber Security Breach: Impact, Investigation, And Mitigation guide to help target audience make the right decision.
Key differences or Key takeways, provide in informative table format
Transition to main article topics
FAQ
This section presents a series of frequently asked questions (FAQs) to address common concerns and misconceptions related to the Cell C cyber security breach. These questions cover various aspects of the incident, including its impact, investigation, and mitigation measures.
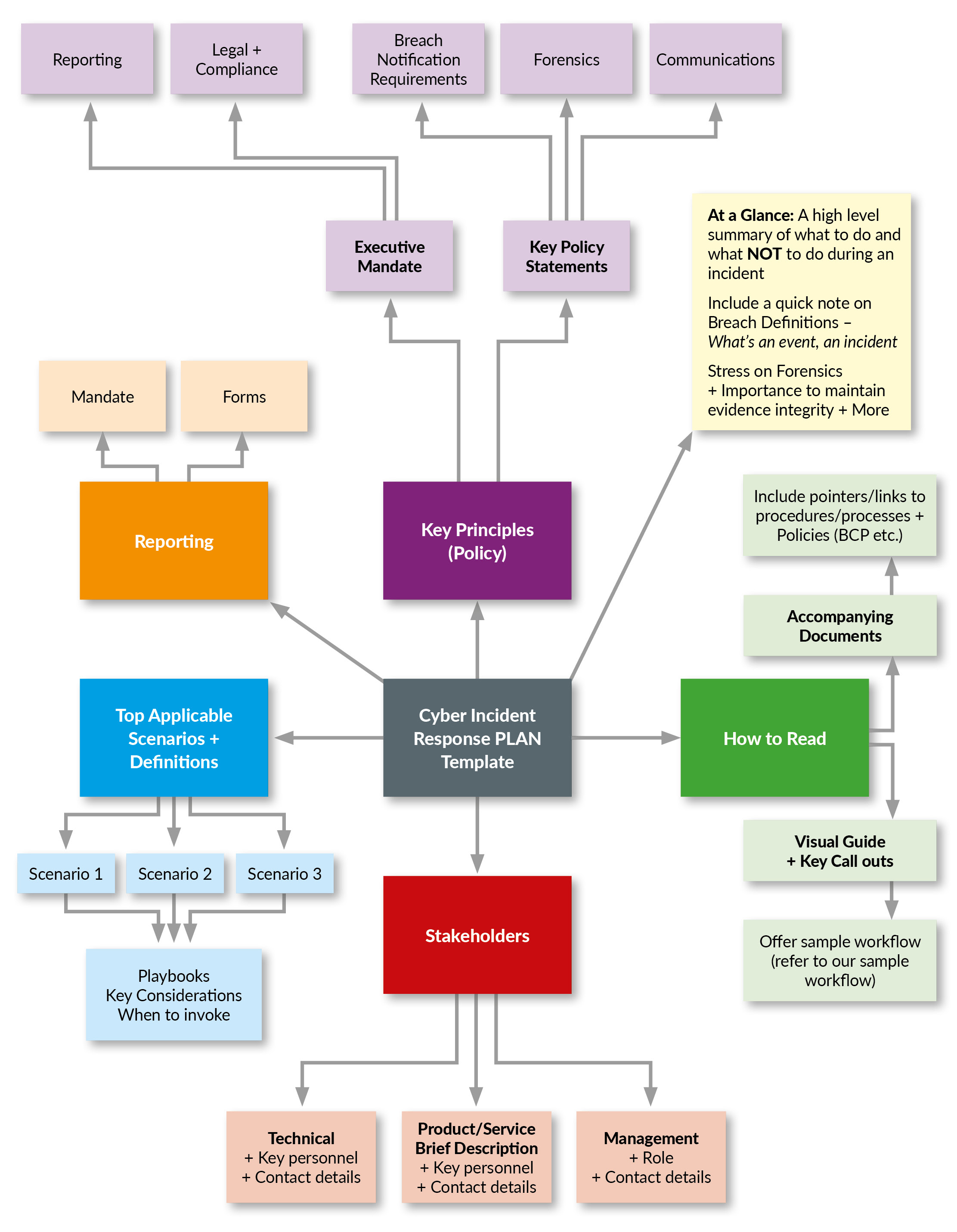
Cyber Security Breach Response Plan Template - Source flamlabelthema.netlify.app
Question 1: What is the nature and extent of the breach?
The breach involved unauthorized access to certain customer information, including names, identity numbers, addresses, and contact details. No financial or payment information was compromised.
Question 2: How did the breach occur?
The investigation is ongoing, but preliminary findings indicate that the breach was likely caused by a sophisticated phishing attack that targeted Cell C employees.
Question 3: What is Cell C doing to mitigate the impact of the breach?
Cell C has taken several steps, including: notifying affected customers, resetting passwords, enhancing security measures to prevent future breaches, and working with law enforcement to investigate the incident.
Question 4: Are there any legal implications for Cell C?
The breach may have legal implications, as it involves the unauthorized disclosure of personal information. Cell C is cooperating with relevant authorities to determine the appropriate course of action.
Question 5: What should affected customers do?
Affected customers are advised to be vigilant for any suspicious activity, such as phishing emails or unauthorized access to their accounts. They should also consider changing their passwords and monitoring their credit reports.
Question 6: How can I get more information about the breach?
Cell C has established a dedicated website and helpline to provide updates and information about the breach. Customers can visit the website or contact the helpline for further assistance.
In conclusion, the Cell C cyber security breach is a serious incident that has impacted the personal information of some customers. The company is taking proactive measures to mitigate the impact and ensure the security of its customers' data.
Moving forward, Cell C remains committed to protecting its customers' privacy and data. The company will continue to invest in robust security measures and work with industry experts to prevent future breaches.
Tips
The Cell C Cyber Security Breach: Impact, Investigation, And Mitigation article highlights the importance of cybersecurity measures to protect sensitive data. To mitigate the risk of future breaches, consider implementing the following tips:
Tip 1: Strengthen Password Policies
Enforce complex passwords with a minimum length, character diversity, and regular expiration. Implement two-factor authentication for added security.
Tip 2: Regularly Update Software and Systems
Patching vulnerabilities promptly prevents attackers from exploiting known weaknesses. Automate software updates to minimize downtime and ensure ongoing security.
Tip 3: Deploy Anti-Malware and Anti-Phishing Solutions
Use reputable security software to detect and block malicious software and phishing attempts. Regularly update these solutions to stay ahead of evolving threats.
Tip 4: Educate Employees on Cybersecurity Best Practices
Conduct regular training sessions to raise awareness about cybersecurity risks and best practices. Emphasize the importance of strong passwords, secure browsing habits, and reporting suspicious activity.
Tip 5: Implement Data Encryption
Encrypt sensitive data both at rest and in transit. This makes it inaccessible to unauthorized parties, even if a breach occurs.
Summary of key takeaways or benefits:
- Reduced risk of data breaches
- Enhanced data protection
- Improved compliance with industry regulations
By adhering to these tips, organizations can strengthen their cybersecurity posture and reduce the likelihood of damaging data breaches.
Cell C Cyber Security Breach: Impact, Investigation, And Mitigation
The recent cyber security breach at Cell C, a prominent South African telecommunications provider, has brought to light the critical importance of robust cyber security measures in the digital age. The breach has had a profound impact on Cell C's customers, operations, and reputation. A thorough investigation is underway, and the company is implementing comprehensive mitigation strategies to prevent similar incidents in the future.
- Customer Impact: Data compromise, financial losses, identity theft
- Operational Disruption: Network outages, service interruptions, data loss
- Reputational Damage: Loss of customer trust, negative publicity
- Investigation: Forensic analysis, external expertise, regulatory involvement
- Mitigation: Enhanced firewalls, intrusion detection systems, staff training
- Lessons Learned: Review of existing security protocols, adoption of best practices

SOLUTION: Cybersecurity breach analysis a complete guide - Studypool - Source www.studypool.com
The Cell C cyber security breach serves as a timely reminder of the evolving nature of cyber threats and the need for businesses to prioritize cyber security. By exploring the key aspects of this incident, organizations can gain valuable insights into the potential impact of cyber security breaches, the importance of thorough investigations, and the effectiveness of mitigation strategies. This knowledge empowers businesses to make informed decisions and take proactive steps to safeguard their data, systems, and reputation against future cyber attacks.

Premium Photo | Cybersecurity breach by Russian hacker - Source www.freepik.com
Cell C Cyber Security Breach: Impact, Investigation, And Mitigation
The Cell C cyber security breach of 2022 exposed the personal data of millions of South Africans, including their names, ID numbers, addresses, and phone numbers. The breach was a major blow to Cell C's reputation and raised serious questions about the company's ability to protect its customers' data.

Cybersecurity Breach Warning Sign | Premium AI-generated image - Source www.freepik.com
The breach was caused by a vulnerability in Cell C's website that allowed hackers to access the company's database. The hackers then used this data to create fake Cell C accounts and make fraudulent purchases. Cell C has since patched the vulnerability and is working to improve its security measures.
The breach is a reminder of the importance of cyber security. Businesses need to take steps to protect their customers' data from hackers. This includes investing in security measures, such as firewalls and intrusion detection systems, and educating employees about cyber security risks.
The Cell C breach is also a reminder of the importance of consumer vigilance. Consumers need to be aware of the risks of phishing scams and other cyber attacks. They should also be careful about what information they share online.
By following these tips, businesses and consumers can help to protect themselves from cyber attacks.
Table summarizing the key points of the article:
| Key Point | Explanation |
|---|---|
| The Cell C cyber security breach exposed the personal data of millions of South Africans. | The breach was caused by a vulnerability in Cell C's website that allowed hackers to access the company's database. |
| Cell C has since patched the vulnerability and is working to improve its security measures. | The company is also educating employees about cyber security risks. |
| The breach is a reminder of the importance of cyber security. | Businesses need to invest in security measures and educate employees about cyber security risks. |
| Consumers need to be aware of the risks of phishing scams and other cyber attacks. | They should also be careful about what information they share online. |